|
|
|
|

|
Enrico Cambiaso, Francesco Folino, Massimo Guarascio, Angelica Liguori , Antonino Rullo Journal of Information Security and Applications The increasing sophistication of cyberattacks targeting companies and organizations continues to challenge the effectiveness of modern defense systems. Among these threats, slow Denial-of-Service (slow DoS) attacks are particularly difficult to detect, as they rely on evasion strategies that add significant complexity to cybersecurity efforts. Modern intrusion detection systems, especially those based on deep learning, have become essential tools in combating such attacks. However, their performance is often hindered by challenges such as limited data availability, noisy inputs, and the presence of out-of-distribution samples. Furthermore, their dependence on large labeled datasets makes detecting subtle or rare attack patterns particularly challenging. To overcome these limitations, this work proposes a novel unsupervised deep learning framework for detecting slow DoS attacks. The proposed approach incorporates a customized preprocessing pipeline to improve input data quality and leverages a sparse variational U-Net-like architecture for robust anomaly identification. Extensive experiments conducted on three real-world datasets demonstrate the framework's ability to accurately and efficiently detect slow DoS attacks, highlighting its robustness, generalizability, and practical suitability for deployment in operational environments. [ Paper ] |
|
|

|
Angelica Liguori , Marco Zuppelli, Daniela Gallo, Massimo Guarascio, Luca Caviglione Journal of Intelligent Information Systems Malware is increasingly endowed with steganographic mechanisms for concealing malicious data to avoid detection or bypass security measures. As a result, an emerging wave of threats named stegomalware has started to rise. Among the various approaches, real-world stegomalware primarily hides information within digital images, for instance, to retrieve additional payloads or configuration data. Unfortunately, developing attack-agnostic mitigation tools is difficult, especially due to the tight relation between the image format and the steganographic technique. Therefore, this paper presents an autoencoder-based approach to perform sanitization, i.e., to disrupt the malicious content hidden in images without altering their visual quality. For this purpose, we used an enhanced U-Net-like neural architecture, and we compared our idea against other mechanisms, including JPG transcoding and simple addition of Gaussian noise. Results obtained by considering different hiding patterns and realistic payloads showcased the effectiveness of our approach. Moreover, the U-Net-based sanitization solution prevents the recovery of the payload while preserving the original image quality and reducing risks arising from side-channel attacks. |
|
|
|
|
|
Nunziato Cassavia, Luca Caviglione, Massimo Guarascio, Angelica Liguori , Marco Zuppelli Journal of Intelligent Information Systems Modern IoT ecosystems are the preferred target of threat actors wanting to incorporate resource-constrained devices within a botnet or leak sensitive information. A major research effort is then devoted to create countermeasures for mitigating attacks, for instance, hardware-level verification mechanisms or effective network intrusion detection frameworks. Unfortunately, advanced malware is often endowed with the ability of cloaking communications within network traffic, e.g., to orchestrate compromised IoT nodes or exfiltrate data without being noticed. Therefore, this paper showcases how different autoencoder-based architectures can spot the presence of malicious communications hidden in conversations, especially in the TTL of IPv4 traffic. To conduct tests, this work considers IoT traffic traces gathered in a real setting and the presence of an attacker deploying two hiding schemes (i.e., naive and “elusive” approaches). Collected results showcase the effectiveness of our method as well as the feasibility of deploying autoencoders in production-quality IoT settings. |
|
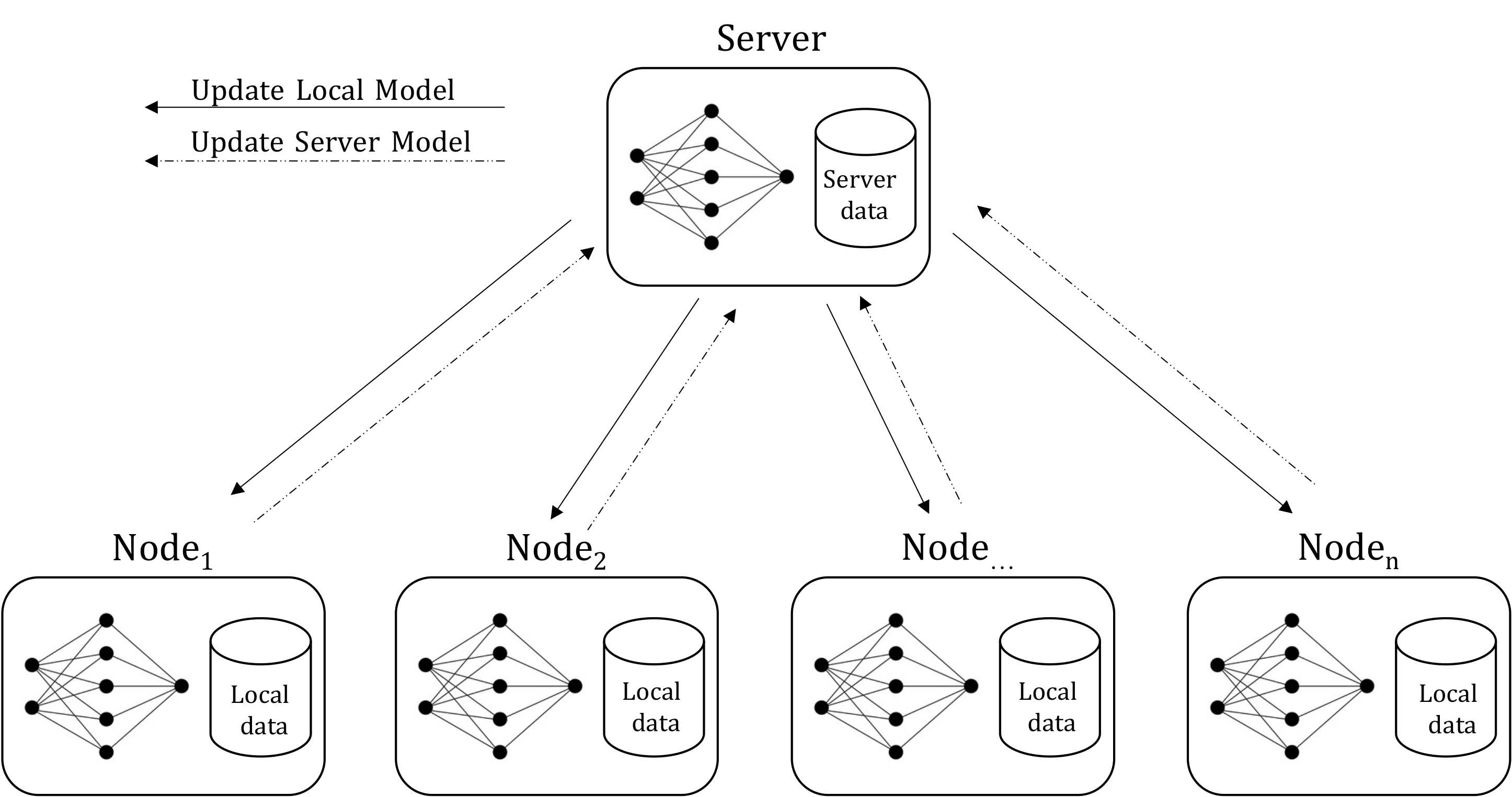
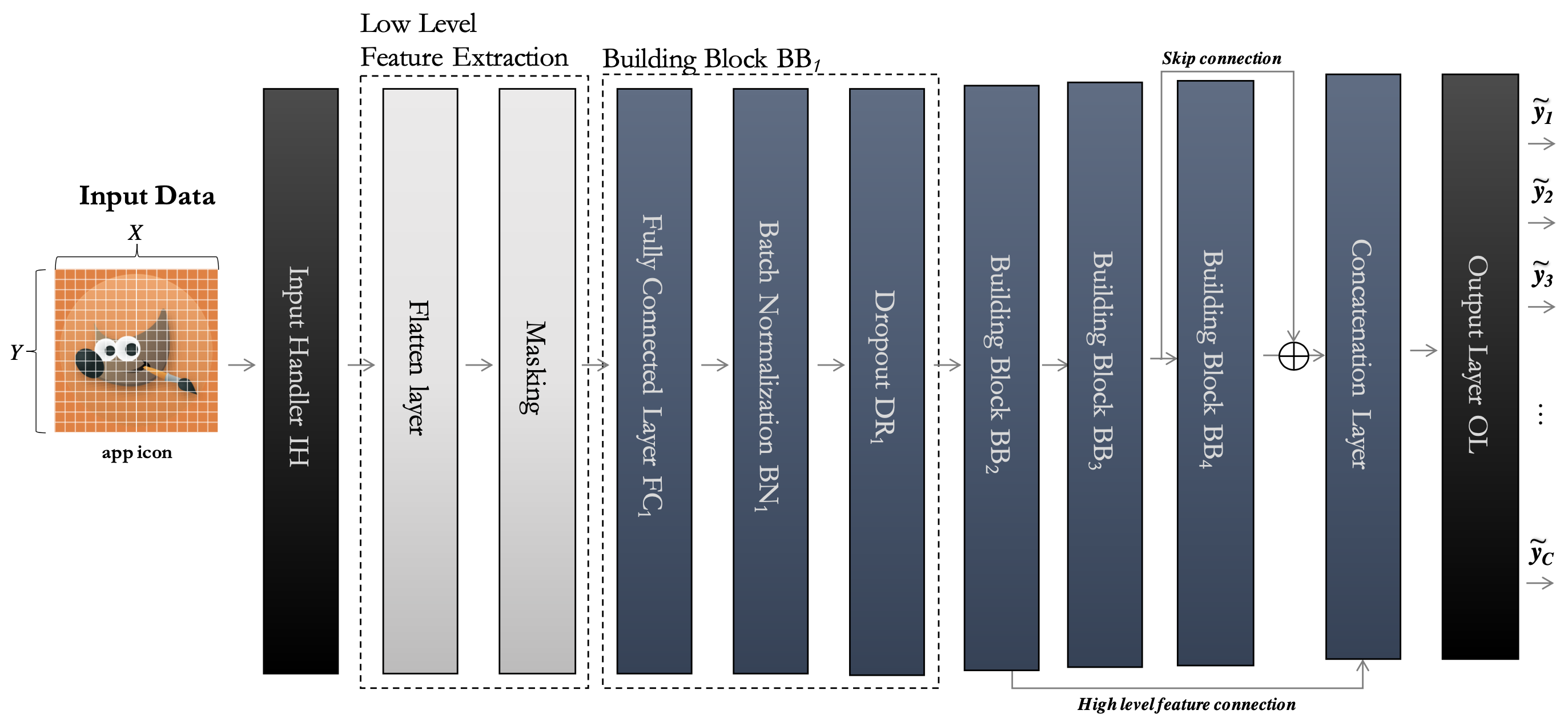
Nunziato Cassavia, Luca Caviglione, Massimo Guarascio, Angelica Liguori , Giuseppe Manco, Marco Zuppelli Social Network Analysis and Mining An increasing volume of malicious software exploits information hiding techniques to cloak additional attack stages or bypass frameworks enforcing security. This trend has intensified with the growing diffusion of mobile ecosystems, and many threat actors now conceal scripts or configuration data within high-resolution icons. Even if machine learning has proven to be effective in detecting various hidden payloads, modern mobile scenarios pose further challenges in terms of scalability and privacy. In fact, applications can be retrieved from multiple stores or directly from the Web or social media. Therefore, this paper introduces an approach based on federated learning to reveal information hidden in high-resolution icons bundled with mobile applications. Specifically, multiple nodes are used to mitigate the impact of different privacy regulations, the lack of comprehensive datasets, or the computational burden arising from distributed stores and unofficial repositories. Results collected through simulations indicate that our approach achieves performances similar to those of centralized blueprints. Moreover, federated learning demonstrated its effectiveness in coping with simple “obfuscation” schemes like Base64 encoding and zip compression used by attackers to avoid detection. |
|
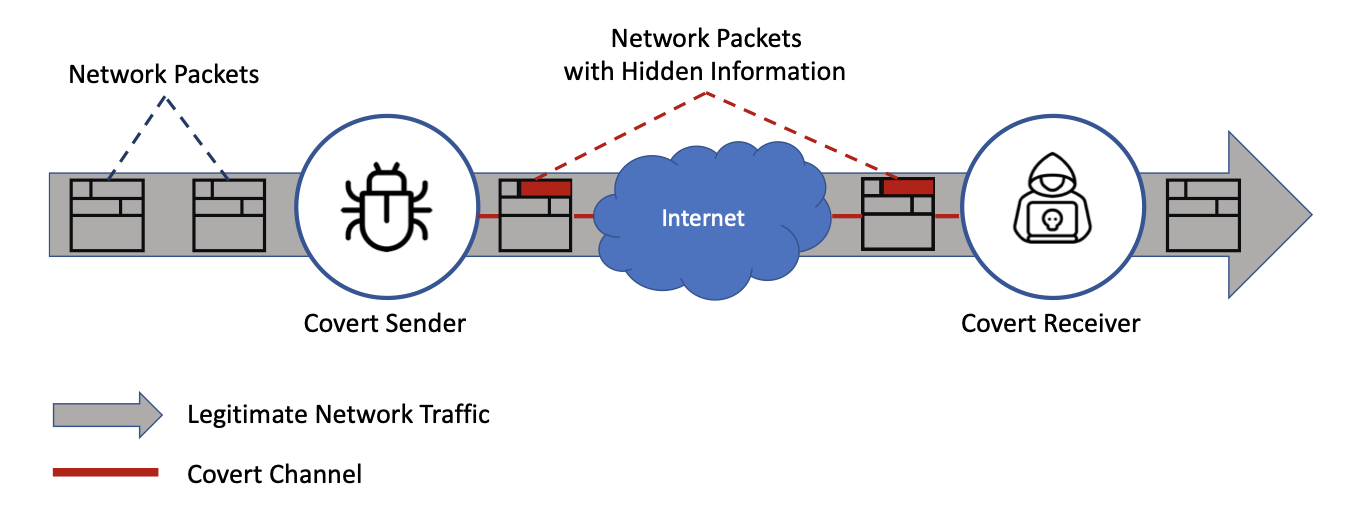
Angelica Liguori , Simone Mungari, Marco Zuppelli, Carmela Comito, Enrico Cambiaso, Matteo Repetto, Massimo Guarascio, Luca Caviglione, Giuseppe Manco Ital-IA 2023: 3rd National Conference on Artificial Intelligence Recently, the number of attacks aiming at breaching networked and softwarized environments has been growing exponentially. In particular, information hiding methods and covert attacks have been proven to be able to elude traditional detection systems and exfiltrate sensitive data without producing visible network flows or data exchanges. In this context, Artificial Intelligence techniques can play a key role in detecting these new emerging attacks, owing to their capability of quickly processing huge amounts of data without the necessity of expert intervention. In this work, we discuss the main challenges to face covert attacks in IoT and softwarized environments and we describe some preliminary results obtained by adopting Deep Learning architectures. [ Paper ] |
|
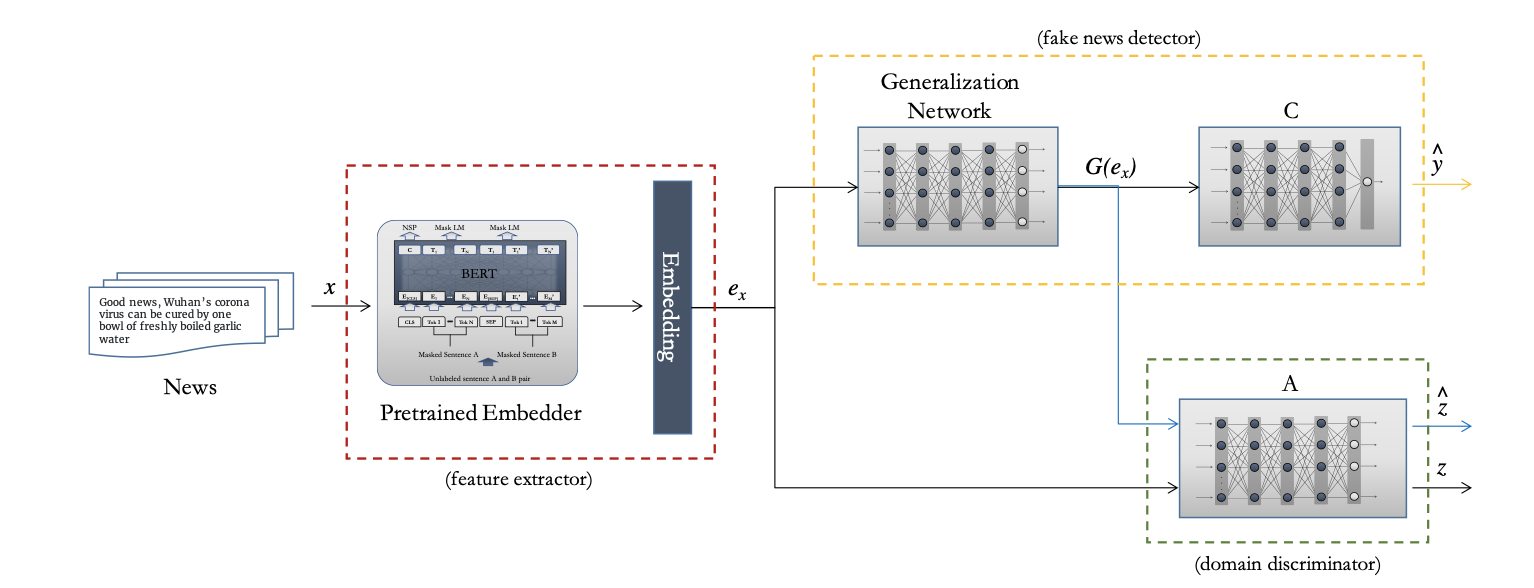
Carmela Comito, Francesco Sergio Pisani, Erica Coppolillo, Angelica Liguori , Massimo Guarascio, Giuseppe Manco ITASEC 2023: The Italian Conference on CyberSecurity Twitter, Facebook, and Instagram are just some examples of social media currently used by people to share news with other users worldwide. However, the information widespread through these channels is typically unverified and/or interpreted according to the user’s point of view. Accordingly, those means represent the perfect tool to hack user opinions with misleading or false news and make fake news viral. Identifying this malicious information is a crucial but challenging task since fake news can concern different topics. Indeed, the detection models learned against a specific domain will exhibit poor performances when tested on a different one. In this work, we propose a novel deep learning-based architecture able to mitigate this problem by yielding cross-domain high-level features for addressing this task. Preliminary experimentation conducted on two benchmarks demonstrated the validity of the proposed solution. [ Paper ] |
|
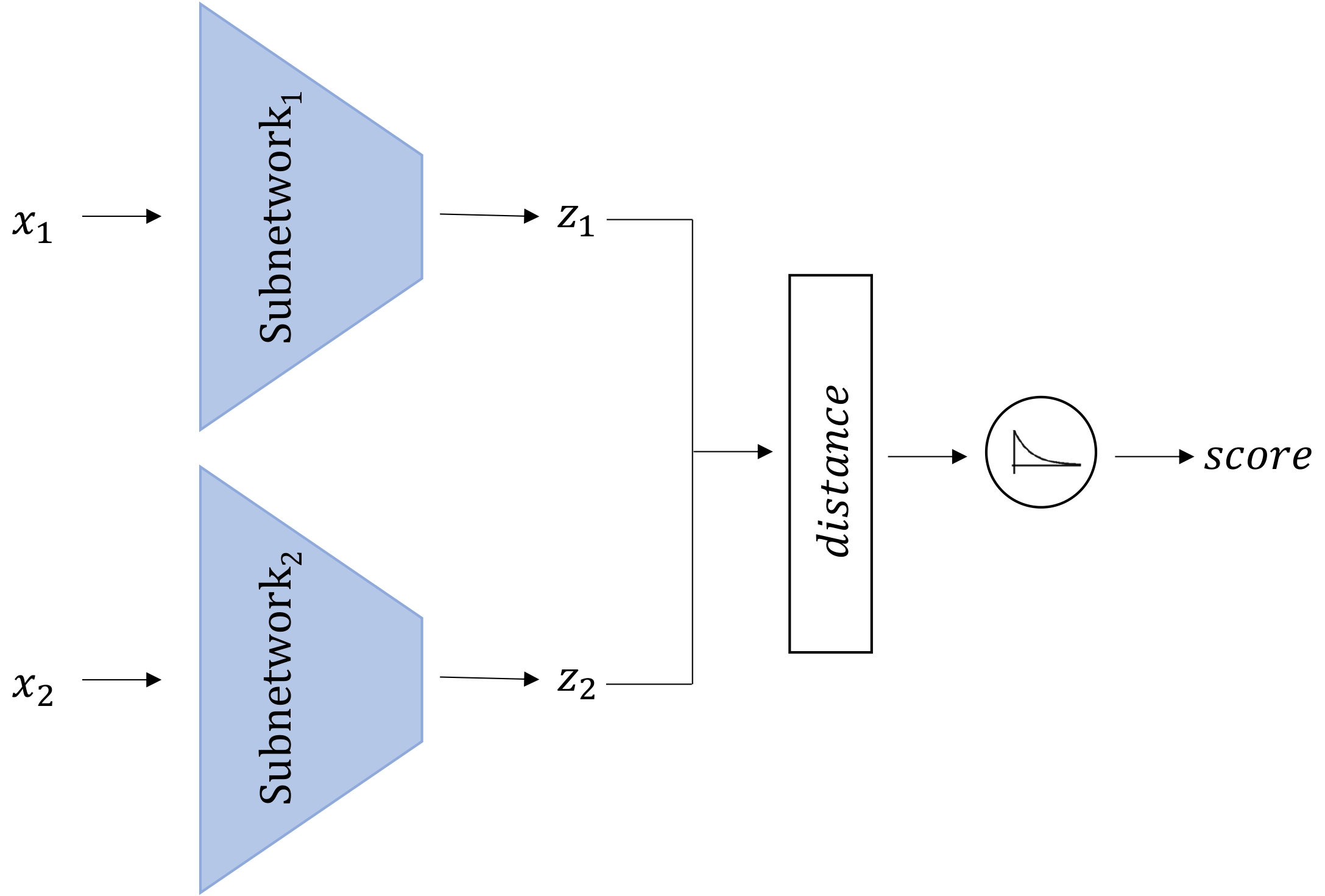
Erica Coppolillo, Daniela Gallo, Angelica Liguori , Simone Mungari, Ettore Ritacco, Giuseppe Manco SEBD 2023: 31st Symposium on Advanced Database System Currently, most multimedia users choose to purchase items through e-commerce. Nevertheless, one of the main concerns of online shopping is the possibility of obtaining counterfeit products. Therefore, it is crucial to monitor the authenticity of the product, thus adopting an automatic mechanism to validate the similarity between the purchased item and the delivered one. To overcome this issue, we propose a Siamese Network model for detecting forged items. Preliminary experimentation on a publicly available dataset proves the effectiveness of our solution. [ Paper, Slides ] |
|
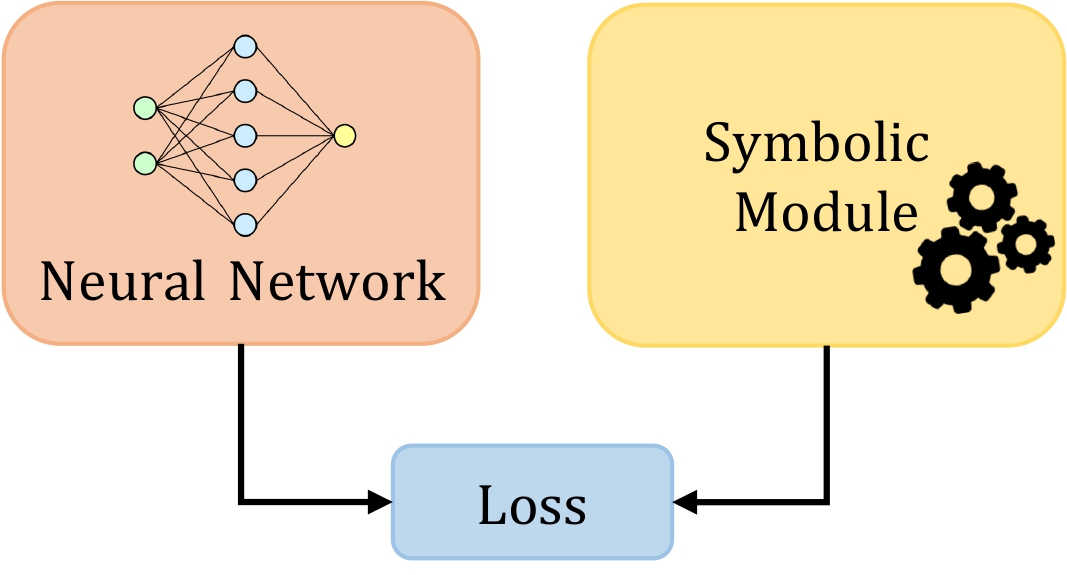
Angelica Liguori , Simone Mungari, Ettore Ritacco, Francesco Ricca, Giuseppe Manco, Salvatore Iiritano SEBD 2023: 31st Symposium on Advanced Database System Predictive maintenance plays a key role in the core business of the industry due to its potential in reducing unexpected machine downtime and related cost. To avoid such issues, it is crucial to devise artificial intelligence models that can effectively predict failures. Predictive maintenance current approaches have several limitations that can be overcome by exploiting hybrid approaches such as Neuro-Symbolic techniques. Neuro-symbolic models combine neural methods with symbolic ones leading to improvements in efficiency, robustness, and explainability. In this work, we propose to exploit hybrid approaches by investigating their advantage over classic predictive maintenance approaches. [ Paper, Poster ] |
|
Angelica Liguori , Luciano Caroprese, Marco Minici, Bruno Veloso, Francesco Spinnato, Mirco Nanni, Giuseppe Manco, Joao Gama arXiv In real-world scenario, many phenomena produce a collection of events that occur in continuous time. Point Processes provide a natural mathematical framework for modeling these sequences of events. In this survey, we investigate probabilistic models for modeling event sequences through temporal processes. We revise the notion of event modeling and provide the mathematical foundations that characterize the literature on the topic. We define an ontology to categorize the existing approaches in terms of three families: simple, marked, and spatio-temporal point processes. For each family, we systematically review the existing approaches based based on deep learning. Finally, we analyze the scenarios where the proposed techniques can be used for addressing prediction and modeling aspects. |
|
|
|
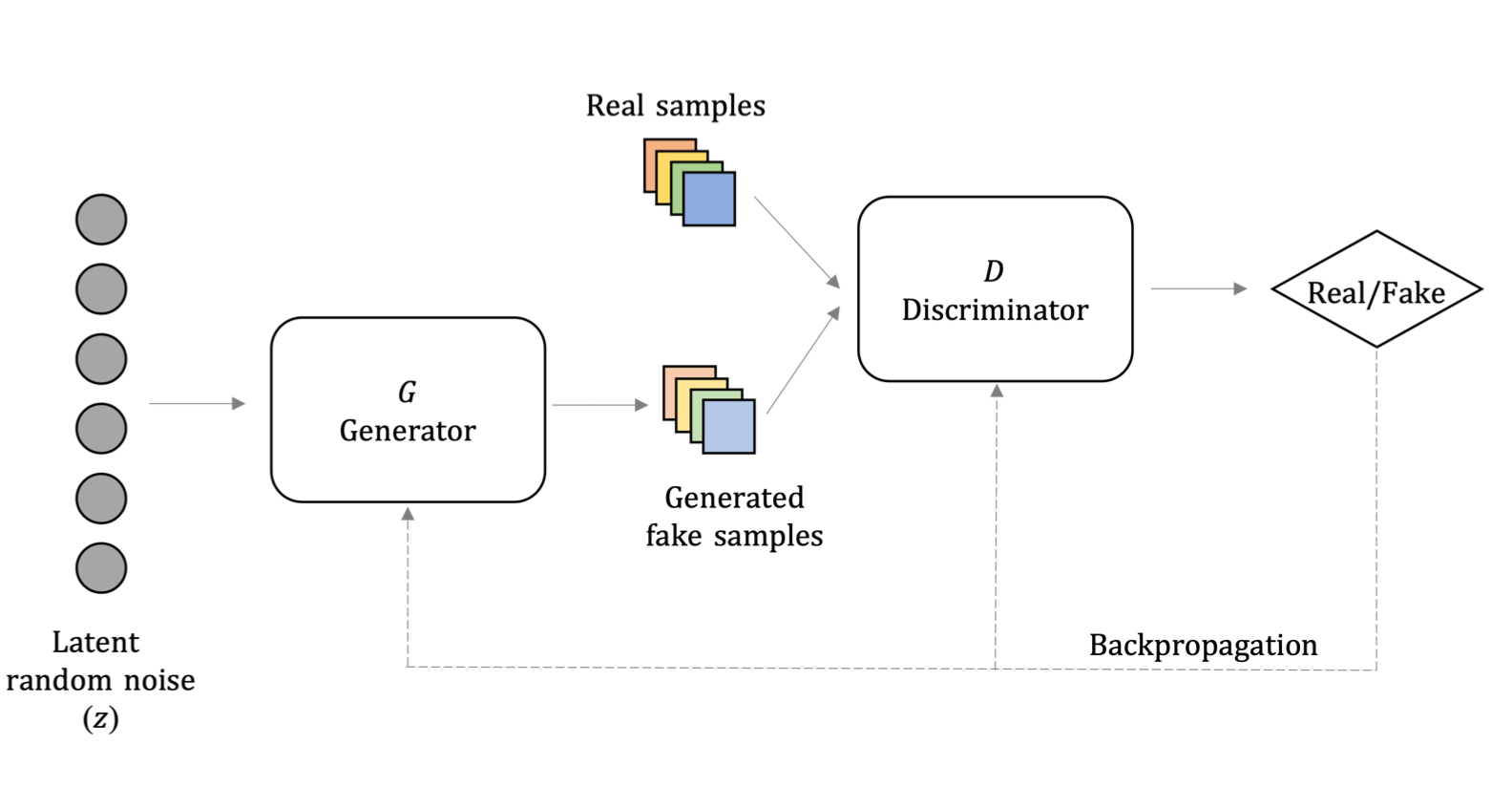
Erica Coppolillo, Angelica Liguori , Massimo Guarascio, Francesco Sergio Pisani, Giuseppe Manco Digital Sovereignty in Cyber Security: New Challenges in Future Vision Part of the Communications in Computer and Information Science book series (CCIS,volume 1807) In recent times, Machine Learning has played an important role in developing novel advanced tools for threat detection and mitigation. Intrusion Detection, Misinformation, Malware, and Fraud Detection are just some examples of cybersecurity fields in which Machine Learning techniques are used to reveal the presence of malicious behaviors. However, Out-of-Distribution, i.e., the potential distribution gap between training and test set, can heavily affect the performances of the traditional Machine Learning based methods. Indeed, they could fail in identifying out-of-samples as possible threats, therefore devising robust approaches to cope with this issue is a crucial and relevant challenge to mitigate the risk of undetected attacks. Moreover, a recent emerging line proposes to use generative models to yield synthetic likely examples to feed the learning algorithms. In this work, we first survey recent Machine Learning and Deep Learning based solutions to face both the problems, i.e., outlier detection and generation; then we illustrate the main cybersecurity application scenarios in which these approaches have been adopted successfully. |
|
Nunziato Cassavia, Luca Caviglione, Massimo Guarascio, Angelica Liguori , Giuseppe Surace, Marco Zuppelli EAI PerSoM 2022 - EAI International Conference on Pervasive knowledge and collective intelligence on Web and Social Media Best Paper Award! An increasing number of threat actors takes advantage of information hiding techniques to prevent detection or to drop payloads containing attack routines. With the ubiquitous diffusion of mobile appli- cations, high-resolution icons should be considered a very attractive carrier for cloaking malicious information via steganographic mechanisms. Despite machine learning approaches proven to be effective to detect hidden payloads, the mobile scenario could challenge their deployment in realistic use cases, for instance due to scalability constraints. Therefore, this paper introduces an approach based on federated learning able to prevent hazards characterizing production-quality scenarios, including different privacy regulations and lack of comprehensive datasets. Numerical results indicate that our approach achieves performances similar to those of centralized solutions. |
|
Nunziato Cassavia, Luca Caviglione, Massimo Guarascio, Angelica Liguori , Marco Zuppelli International Symposium on Methodologies for Intelligent Systems, ISMIS 2022 Foundations of Intelligent Systems Part of the Lecture Notes in Computer Science book series (LNAI,volume 13515) Network covert channels are becoming exploited by a wide-range of threats to avoid detection. Such offensive schemes are expected to be also used against IoT deployments, for instance to exfiltrate data or to covertly orchestrate botnets composed of simple devices. Therefore, we illustrate a solution based on Deep Learning for the detection of covert channels targeting the TTL field of IPv4 datagrams. To this aim, we take advantage of an Autoencoder ensemble to reveal anomalous traffic behaviors. An experimentation on realistic traffic traces demonstrates the effectiveness of our approach. |
|
|
|
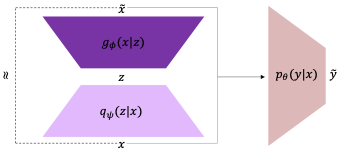
Angelica Liguori , Giuseppe Manco, Francesco Sergio Pisani, Ettore Ritacco 2021 IEEE International Conference on Data Mining (ICDM) We propose ARN, a semisupervised anomaly detection and generation method based on adversarial reconstruction. ARN exploits a regularized autoencoder to optimize the reconstruction of variants of normal examples with minimal differences, that are recognized as outliers. The combination of regularization and adversarial reconstruction helps to stabilize the learning process, which results in both realistic outlier generation and substantial detection capability. Experiments on several benchmark datasets show that our model improves the current state-of-the-art by valuable margins because of its ability to model the true boundaries of the data manifold. [ Slides ] |
|
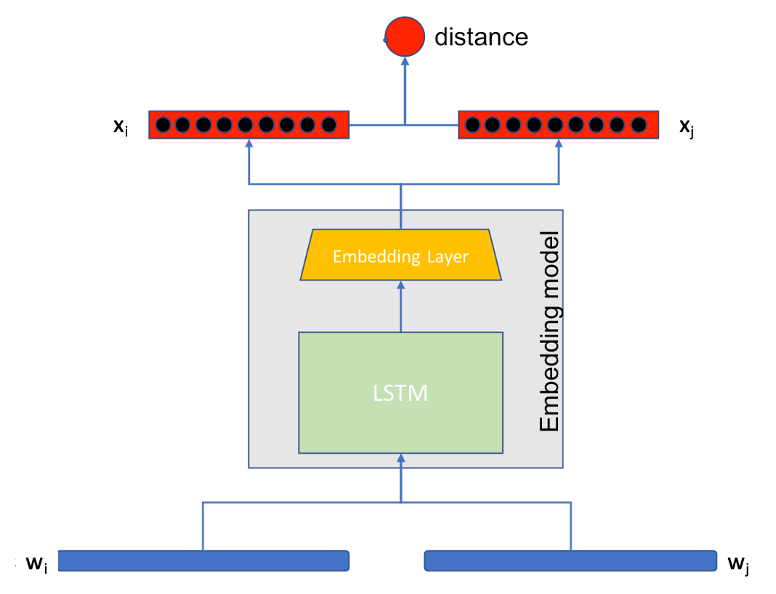
Angelica Liguori , Giuseppe Manco, Ettore Ritacco, Massimilano Ruffolo, Salvatore Iiritano SEBD 2021: The 29th Italian Symposium on Advanced Database Systems We propose an unsupervised anomaly detection model that is able to identify abnormal behavior by analysing streaming data coming from IoT sensors installed on critical devices. The proposed model is based on a Siamese neural network which embeds time series windows in a latent space, thus generating distance-based clusters of normal behavior [ Paper ] |
|
|
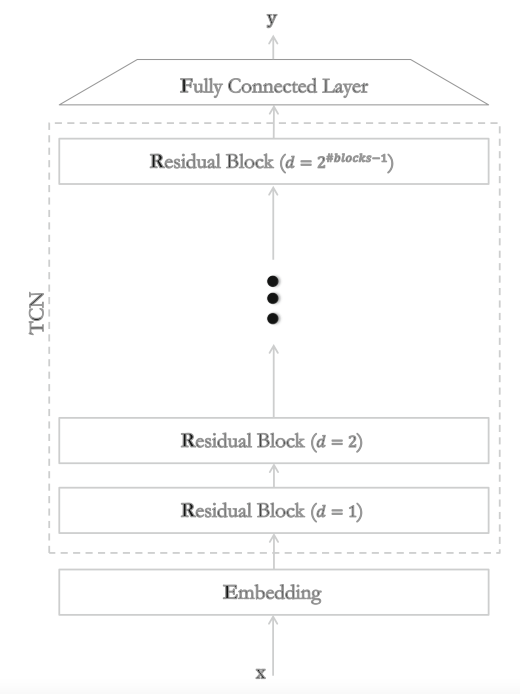
|
Francesco Folino, Massimo Guarascio, Angelica Liguori , Giuseppe Manco, Luigi Pontieri, Ettore Ritacco ECML PKDD: Joint European Conference on Machine Learning and Knowledge Discovery in Databases, 2020 Part of the Communications in Computer and Information Science book series (CCIS, volume 1323), Springer International Publishing We propose a novel convolution-based deep learning approach to the prediction of the next activity which relies on: (i) extracting high-level features (at dif- ferent levels of abstraction) through the computation of time-oriented dilated convolutions over traces, and (ii) exploiting residual-like con- nections to make the training of the predictive model more robust and faster. [ Paper ] |
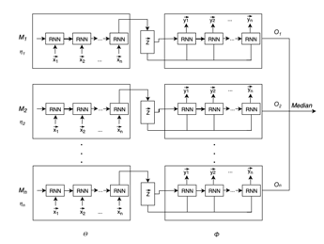
|
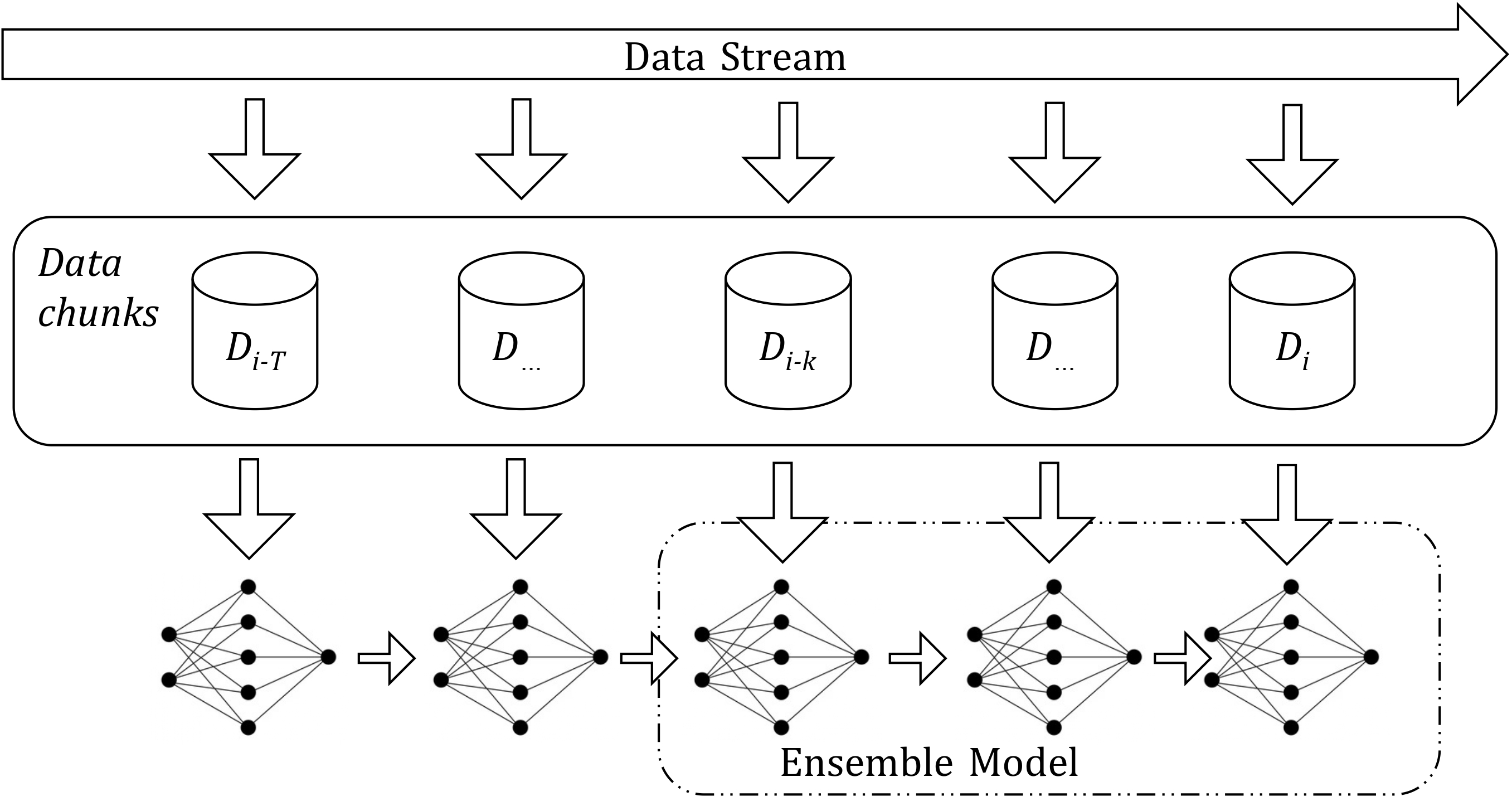
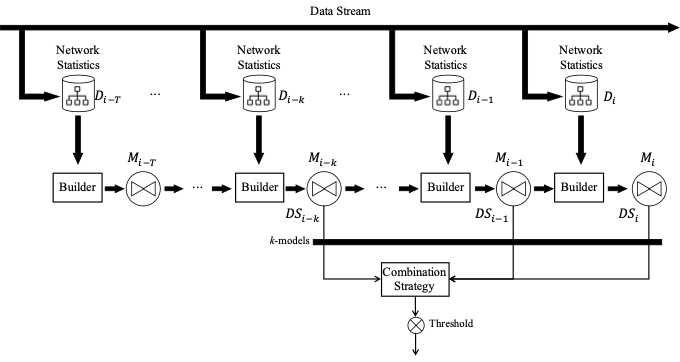
Francesco Scicchitano, Angelica Liguori , Massimo Guarascio, Ettore Ritacco, Giuseppe Manco 25th International Symposium on Methodologies for Intelligent Systems, ISMIS 2020 Foundations of Intelligent Systems Part of the Lecture Notes in Computer Science book series (LNCS, volume 12117), Springer International Publishing We propose an Ensemble Deep Learning approach to detect deviant behaviors on Blockchain where the base learner, an encoder-decoder model, is strengthened by iteratively learning and aggregating multiple instances, to compute an outlier score for each observation. [ Paper, Slides ] |
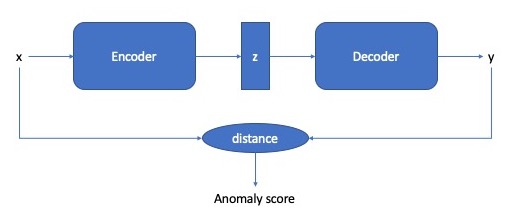
|
Francesco Scicchitano, Angelica Liguori , Massimo Guarascio, Ettore Ritacco, Giuseppe Manco Italian Conference on CyberSecurity, ITASEC 2020 We define an anomaly detection system based on a encoder-decoder deep learning model, that is trained exploiting aggregate information extracted by monitoring blockchain activities. [ Paper ] |